A core competency of SōtirIS Information Strategies is delivering secure mobile workforce technologies. We have partnered with leading security technology partners to provide enterprise-grade security solutions that encompass the entire computing experience. Our security solutions support the data center, office user, and the mobile user.
Businesses make decisions every day that negatively impact their security readiness—for example, refusing to shut down a server for proper patching, or choosing to keep working on old hardware and software to save budget. IT leaders need to be sure that invisible systemic risk is recognized, reported, and discussed in governance processes.

While organizations have understood for more than a decade that security is a business problem, they continue to struggle with approaching it as one. Its treatment remains largely a technical problem, handled by technical people and buried in IT, even though it has been presented in the boardroom at least annually for years.
The Growing Risk with Insecure Office Environments
There is increasing evidence that hackers are preying on individuals that are working outside secure office environments. Cyber vulnerabilities have increased dramatically due to the huge numbers of people now working remotely.
The trusted advisors at SōtirIS have the expertise to design and deliver a 360-degree security solution that will protect your organization’s information and knowledge. Our industry-leading solutions include:
- Active Directory Management
- Multi-Factor Authentication
- Vulnerability and Patch Management
- Email Security
- Data Backup and Retention
- Compliance
Multi-Factor Authentication
In the past, one only needed a password to gain access. Now, administrators and users can use a combination of tools and policies that allow seamless authentication while still safeguarding against the most common types of attacks.
One of the most important elements is two-factor authentication (2FA). It is a cost-effective measure that protects against key threat vectors. Two-factor authentication means that whatever application or service you are logging into is double-checking that the request is really coming from you by confirming the login with you through a separate venue.

2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords. If a password is hacked, guessed, or even phished, that is no longer enough to give an intruder access: Without approval at the second factor, a password alone is useless.
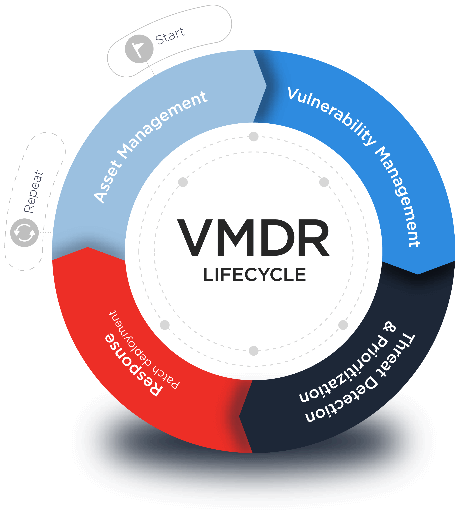
Vulnerability and Patch Management
SōtirIS has partnered with Qualys, Inc.—a leading provider of information security and compliance cloud solutions. We can deliver this solution as a managed service (Security as a Service) or as a hybrid solution (self-service). The heart of this solution is the Asset Scan that identifies the devices connected to your network and the Discovery Scan that reports the vulnerabilities (and severity) associated with those devices.
Patch Management can detect missing patches and deploy patches to your endpoint devices whether they are on-premise, roaming, or remote. Patches can be planned and deployed on a scheduled basis or immediate deployment can be initiated for Zero-day vulnerabilities.
Addressing Evolving Vulnerabilities
Every year, thousands of new vulnerabilities are discovered, requiring organizations to patch operating systems (OS) and applications and reconfigure security settings throughout the entirety of their network environment. To proactively address vulnerabilities before they are utilized for a cyberattack, organizations serious about the security of their environment perform vulnerability management to provide the highest levels of security posture possible.
Vulnerability management is generally defined as the process of identifying, categorizing, prioritizing, and resolving vulnerabilities in operating systems (OS), enterprise applications (whether in the cloud or on-premises), browsers, and end-user applications. An ongoing process, vulnerability management seeks to continually identify vulnerabilities that can be remediated through patching and configuration of security settings.
Top-Rated Vulnerability Management
The IT consultants at SōtirIS will work with your Information Technology Security team to complete the Asset Discovery and Vulnerability scans to generate a baseline of your vulnerability posture. Our consultants will then design an ongoing vulnerability and patch management schedule. Our Vulnerability and Patch Management service is very much a collaborative effort with your IT security team to continually improve your vulnerabilities posture while preventing business operations disruption.
SIX POINT PROCESS
Email Security, Data Backup, & Information Retention
Barracuda Networks is SōtirIS’ go-to partner for email security; data backup; and information retention. Our consultants will work with your team to design, configure, and tweak the email security solution.
Advanced Email Security
Email Continuity
and Data Loss Prevention
Advanced threat protection sandboxes suspicious email attachments and scans them for malware. Link protection redirects suspicious and typo-squatted URLs, so malware is never inadvertently downloaded by recipients.
AI Involvement
Sentinel’s unique API-based architecture lets its AI engine study historical email and learn users’ unique communication patterns. It can then identify anomalies in message metadata and content, to find and block socially engineered attacks in real time.
Preventing Phishing Attacks
Sentinel stops phishing attacks used to harvest credentials for account takeover. It detects anomalous email behavior and alerts IT, then finds and removes all fraud emails sent from compromised accounts.
Sentinel helps prevent email domain fraud with DMARC (Domain-based Message Authentication Reporting and Conformance) reporting and analysis.
Backup and Retention
Barracuda Backup
Barracuda Backup combines storage, software, and inline deduplication to ensure your data is protected against loss no matter what happens. There are no per-application or per-agent licensing fees, and its single-pane-of-glass admin console makes management fast and easy.
Fit to Your Needs
Available as a hardware or virtual appliance, this solution delivers near continuous data protection and replication to an off-site appliance or to the cloud.
Cloud-to-Cloud Backup
The system provides comprehensive, cost-effective, scalable protection for your Office 365 data. It automatically backs up all your email, OneDrive for Business, SharePoint, Groups, and Teams data to Barracuda Cloud Storage. And when time is of the essence, restoring what you need takes just a few clicks.
Avoid Restoration Downtime
Microsoft Office 365 retains deleted data in the recycle bin—but only for 93 days. And restoring entire folders or mailboxes is a tedious, manual process—and if the data you need is mission-critical, that means costly downtime that you cannot afford.

Information Retention
The Cloud Archiving Service provides secure cloud-based archiving, helping you meet demanding compliance requirements and address e-discovery requests easily and effectively. It uses the Barracuda Cloud to store data for as long as needed without risk of amendment or deletion. It increases user productivity by making it easy to access every message ever sent or received, from any device.

